Engineers and computer scientists show how bad actors can exploit browser-based control systems in industrial facilities with easy-to-deploy, difficult-to-detect malware.

Web-based tools for industrial systems and critical infrastructure are opening a new pathway for bad actors to attack and seize control of those systems. Increasingly, devices like tablet computers can be used throughout a facility to manage and control these systems.
In recent years, browser and web-based technology has become a powerful tool for operators of infrastructure and industrial systems. But it also has opened a new pathway for bad actors to seize control of these systems, potentially endangering critical power, water, and other infrastructure.
Georgia Tech researchers have found a way to hijack the computers that control these physical systems. Called programmable logic controllers (PLCs), they increasingly have embedded webservers and are accessed on site via web browsers. Attackers can exploit this approach and gain full access to the system.
That means they could spin motors out of control, shut off power relays or water pumps, disrupt internet or telephone communication, or steal critical information. They could even launch weapons — or stop the launch of weapons.
“We think there is an entirely new class of PLC malware that's just waiting to happen. We're calling it web-based PLC malware. And it gives you full device and physical process control,” said Ryan Pickren, a Ph.D. student in the School of Electrical and Computer Engineering (ECE) and the lead author of a new study describing the malware and its implications.
The research team will present their findings Feb. 29 at the 2024 Network and Distributed Systems Security Symposium.
“This has been a neglected attack surface for many years. This paper is going to be the first one where we're exploring what could an adversary to do with this,” Pickren said.
The researchers developed an approach that’s easier to deploy than typical attacks on industrial or infrastructure systems, which usually require some sort of access privileges or on-site presence. It’s difficult to detect, with the ability to wreak havoc and then erase all traces of its presence. And it’s sticky: the malware can resurrect itself if operators discover the malfunctions and reset controllers or even replace hardware.
“We believe this is one of the first attacks at the application layer of PLCs to compromise industrial systems,” said Raheem Beyah, senior author on the study, a professor in ECE, and dean of the College of Engineering. “This is opening a door to a new field that hasn’t really been studied yet.”
This new cyberattack strategy is the result of a shift in recent years in software and devices used to control and monitor various industrial systems. Instead of a dedicated terminal or control pad running custom software specific to the device, manufacturers have turned to web-based management. Now, devices have embedded web servers. The human-machine interfaces — think keypads or control panels — are actually mini web browsers rendering a web page with readouts of the current status and digital visualizations of the controls.
The approach means operators can work on the go, using a tablet computer for example, or even keep tabs on the system off-site.
“The old school idea of Homer Simpson in a control room has now turned into a website where you have little web visualizations,” Pickren said. “You can imagine a worker walking around the facility with an iPad or a control room with Google Chrome open.”
Malware designed to exploit these web vulnerabilities is particularly powerful because it doesn’t have to be customized to a specific PLC before it can be deployed, according to Saman Zonouz, associate professor in ECE and the School of Cybersecurity and Privacy and study co-author. In fact, the research team’s investigation showed their proposed attack would work on PLCs produced by every major manufacturer.
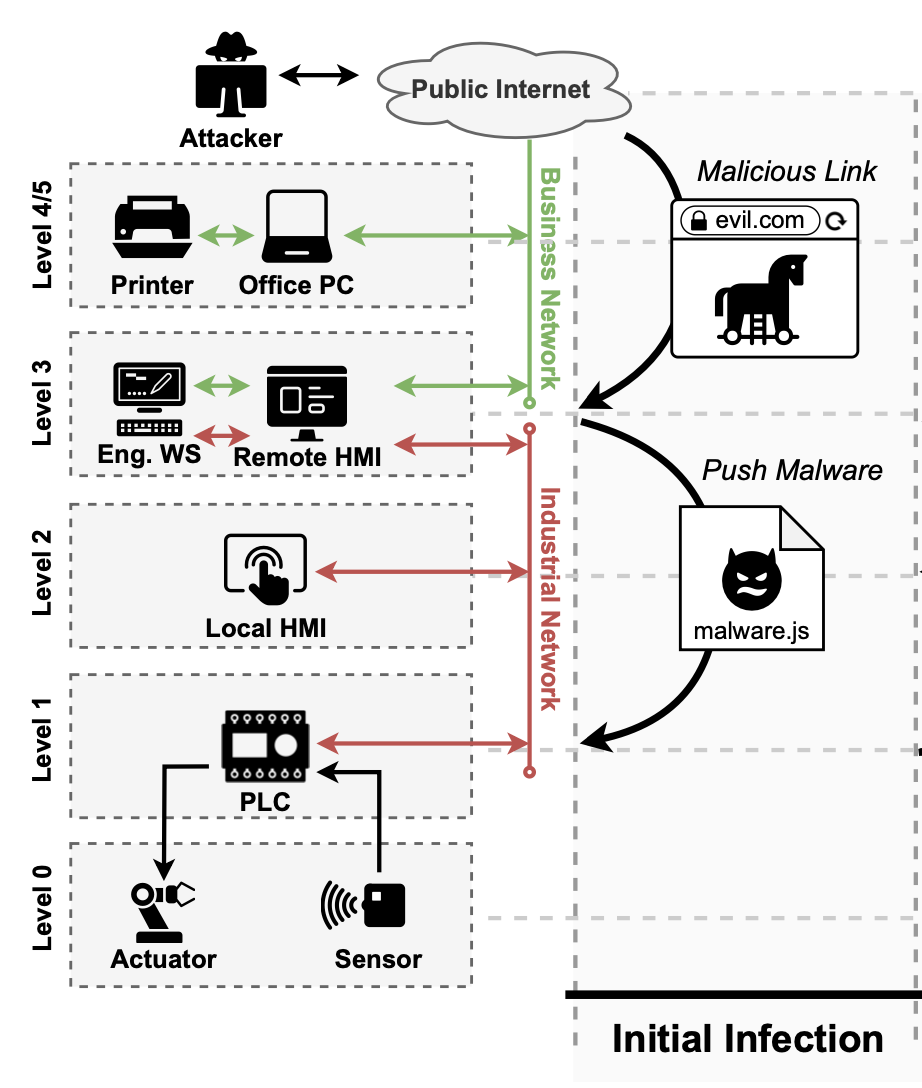
A typical network structure for industrial control systems where the human-machine interface (HMI) — essentially, control panels — and the programmable logic controller (PLC) are isolated from engineering workstations (EWS) and the public internet. In a web-based PLC malware attack, even the isolated systems can be access by malicious code that installs on the PLC and runs through a web browser where control functions are displayed for operators. (Courtesy: Ryan Picken)
That’s a significant advantage over traditional attacks on industrial processes that targeted the PLC device itself or its underlying firmware. The Stuxnet worm that caused centrifuges to fail at an Iranian nuclear enrichment facility starting in 2008, for example, was specifically crafted to work on the PLC those facilities employed. It wouldn’t have been effective against other devices without extensive reconfiguration.
“We don't have to reverse engineer, like Stuxnet or Triton — another very well-known malware — which required lots of effort to analyze a particular device,” Zonouz said. “This approach is very agnostic of the device and much easier to exploit. And hence, much harder to get rid of.”
Another advantage to the type of malware the team developed is how it functions. Though it’s deployed to the PLC, it actually runs only in the web browsers used to control the PLC’s functions. That upends typical approaches to dealing with malicious software that study the device itself to find anomalies.
The type of attack the researchers described is more than theoretical, too. They developed and tested one approach that deployed the malicious program by simply viewing a banner ad on a web page using an iPad. The malware infected a PLC in the lab connected to a small motor, and the researchers were able to cause the motor to spin at unsafe speeds. Meanwhile, the PLC reported the motor was still operating normally.
Pickren and Zonouz said their test showed how easy, and scary, it could be to infect real-world systems. Say a bad actor bought an ad on a popular help forum for PLC users. As soon as an operator visited the page and the ad loaded, their systems could be compromised.

Instead of a dedicated terminal or control pad running custom software specific to the device, manufacturers for industrial and infrastructure systems have turned to web-based management. Now, devices often have embedded web servers. The human-machine interfaces — think keypads or control panels like this — are actually mini web browsers rendering a web page with readouts of the current status and digital visualizations of the controls.
The team identified several vulnerabilities in a popular PLC device that they exploited during their testing. They reported those issues to the manufacturer, which verified and patched the problems.
In their study, the researchers also made several recommendations to protect against web-based PLC malware, including steps browser developers can implement to prevent public access to private networks and webserver architecture changes. They also outlined steps PLC manufacturers can take to harden their devices against this new kind of attack.
“We need to go back and rethink the architectures, the protocols, the deployment that we have in place. How can we make them more secure without getting rid of the interconnectivity, which is a great thing to have,” Zonouz said.
“The internet is a huge attack surface, but everybody uses it and enjoys it. That doesn’t mean we should turn off internet. It means we have to make it more secure. The same thing is true here.”
(text and background only visible when logged in)
About the Research
Citation: Pickren R, Shekari T, Zonouz S, Beyah R. Compromising industrial processes using web-based programmable logic controller malware. NDSS (Feb 26 – Mar 1) 2024. https://dx.doi.org/10.14722/ndss.2024.23049
This research was supported by the National Science Foundation Cyber-Physical Systems program and the Department of Energy Office of Cybersecurity, Energy Security, and Emergency Response. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of any funding agency.

Preeminence in Research
Related Content

Critical Vulnerabilities Allow Hackers to Take Full Control of Wago PLCs
Industrial automation solutions provider Wago has released patches for several of its programmable logic controllers (PLCs) to address four vulnerabilities discovered and reported by Georgia Tech researchers. The vulnerabilities could be exploited to take full control of the targeted device.

Cyber Faculty Sets Out to Protect Nation’s Investment in AI Manufacturing
As part of a $65 million investment in the Georgia AI Manufacturing Technology Corridor, Saman Zonouz is developing a roadmap to help researchers and industry professional understand the potential cybersecurity risks for new AI manufacturing systems, detect attacks, and respond to them.